Five Chinese mobile payment apps are found to record sensitive information users store on their phones, which can be used to track and monitor personal activities
Five Chinese mobile payment apps record sensitive information users store in their mobile devices, which can be used to track and monitor personal activities, FactWire can reveal.
The five popular Chinese mobile payment apps, WeChat, Taobao, Taobao World, Alipay and Tmall, were analyzed through program analyses built from open source code. These analyses discovered the apps collect and file users’ sensitive information such as their IMEI, activities and location data, and the specific information is then made available for transferal to servers in mainland China.
China plans to introduce a “social credit system” in five years’ time which will file information including users’ online activities for surveillance. Based on one’s records, the authorities could make decisions that could impact one’s life, such as whether one could receive tax benefits, choose soft beds in trains, get on a flight, exit the borders, etc.
Cybersecurity and hacking experts stated that one could track and monitor users’ activities once the relevant sensitive information is collected. The Office of the Privacy Commissioner for Personal Data (PCPD) said that there are no regulations in Hong Kong that ban the transferal of personal information to places outside Hong Kong.
According to the “Planning Outline for the Construction of a Social Credit System (2014-2020)” issued by China’s State Council, the sincerity of every citizen within Chinese borders in administrative, commercial, social and judicial affairs would be recorded, accessed, scored and filed for the inspection and surveillance of the Government or relevant organizations. The Internet is also included in the scope of the credit system. Since August 2016, app providers must record user logs and keep them for at least 60 days to assist inspection and surveillance by relevant government departments if necessary.
Many smartphone apps commonly used in Hong Kong are developed and operated by Chinese enterprises, leading to concerns about whether relevant laws in mainland China also apply to Hong Kong people. FactWire launched an investigation into the top five Chinese apps on Google Play’s “Top Free in Android Apps” list that are designed for mobile payment or online transaction and are most used by Hong Kong people.
The five apps that collect and transfer Hong Kong users’ private information to servers in the mainland are all Chinese enterprises. WeChat was developed by Chinese app developer Tencent (0700); Taobao, Taobao World and Tmall were developed by Alibaba Group; Alipay is operated by Alibaba Group-related company Ant Financial Services Group. Information from Google Play Hong Kong shows the five apps recorded at least a hundred million downloads in total.
FactWire analyzed the impact of these apps which collect sensitive information with static and dynamic program analysis. A static program analysis looks at an app when it is not running, to analyze the permission acquired under normal circumstances, the presentations of words and numerical values showing basic information and API security risks. A dynamic program analysis runs an app on a virtual machine, observing the files and services that have been accessed, cryptographic actions, the opened network port and the sent files.
FactWire also tracked information flow by adding “taint” tags to sensitive data, then tracking it through the system. When such data reaches its destination, it is compared with the data source. If it matches, it means that the app has collected the sensitive information. Because of technical limitations, the analyses targeted only the apps in the Android system, and not that of the iOS system.
The method is recognised as a way to analyze data flow by Zhang Ke-huan, Assistant Professor from the Department of Information Engineering at the Chinese University of Hong Kong (CUHK), as well as cybersecurity and hacking expert Anthony Lai Cheuk-tung.
Results from the static program analysis showed that five apps acquired the permission to “read the status and identity code of the device” immediately upon installation, which means that the apps could collect and store each user’s sensitive information such as the IMEI (International Mobile Equipment Identity), IMSI (International Mobile Subscriber Identity), ICCID (Integrated Circuit Card ID) and the telephone number of a phone, as well as call status and the telephone number of callers.
Since the apps do not state whether the collection of sensitive information such as the IMSI and IMEI is involved, users would not be aware of the consequences simply by reading the terms upon installation.
The static program analysis results also showed that the five apps could acquire permission to manage or use the fingerprint scanner on a phone, and to store location and audio record data. Users have agreed to the permissions for the apps to read the files upon installation.
Results from the dynamic program analysis showed that the five apps already recorded users’ IMEI into files even when they have not carried out any payment transactions. The files are available for transferal to servers in the mainland. Alipay, Taobao World, Taobao and Tmall record the IMSI simultaneously.
Upon installation, Taobao World sends users’ IMEI and IMSI to Hangzhou Alibaba Advertising Co., Ltd. At the same time, the app records users’ telephone numbers, IMEI, IMSI and ICCID into its files.
According to the permissions acquired during installation of the apps, including permission to read and write files and full internet usage, the files written with users’ sensitive information could be sent to servers of the apps in the mainland.
“Sensitive information” refers to any data that could track and identify a user’s identity, including their telephone number and their phone’s IMEI, IMSI and ICCID. IMEI is a unique smartphone code of 15 numerical digits that serves as a phone ID, giving information such as the factory license, model number, and place of origin, and production serial number. IMSI, commonly stored in SIM cards, refers to the serial number assigned to each device by the telecommunication company to clearly define the service permission of the telecommunication service. ICCID refers to the identification number of each SIM card.
Professor Zhang of CUHK said that IMEI, IMSI and ICCID represents very sensitive information. After acquiring an IMEI, one could access information “such as the location of the device owner, softwares downloaded and services visited”.
ICCID is the code to track a SIM card, and with the ICCID, one can perform location tracking from cell stations, according to Professor Zhang.
Professor Zhang said: “The Signalling System 7 is a very common and old telecommunications system that guarantees almost no security. Therefore, if one gains access to the SS7 signalling system, one could trace, monitor and follow your calls by inserting the ICCID into the system, which could be very dangerous.”
He said users’ activities on mobile devices could be traced and monitored once sensitive information such as the ICCID has been leaked.
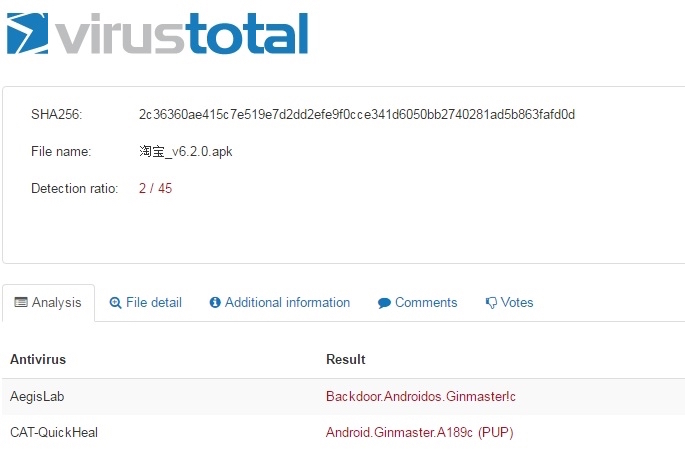
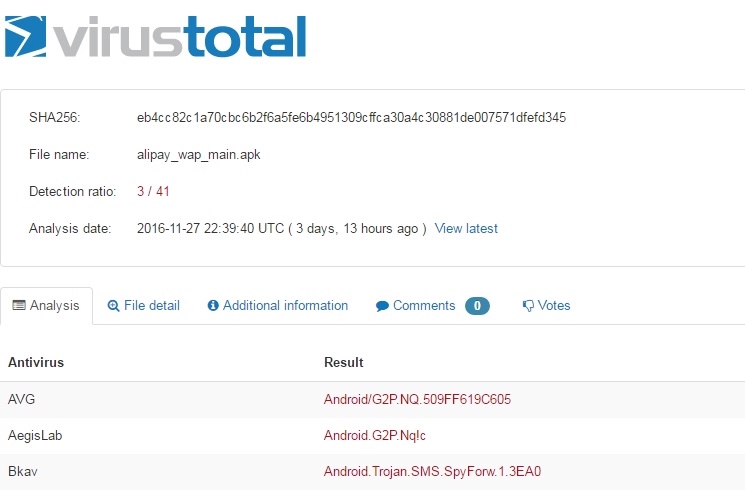
FactWire used VirusTotal, Google’s malware analysis service, to establish whether some smartphone apps contained viruses or malwares. VirusTotal is a scanning engine company that gathers 58 anti-virus engines. VirusTotal showed that the Alipay installation file contained Android Trojan SMS Spy, a Trojan Horse program that could intercept and steal users’ SMS messages. Taobao contains a malware “backdoor.androids.ginmaster”, which could open the backdoor of the mobile device system and steal user’s information without the knowledge of the user.
Three other online transactions apps, Android Pay, Google Wallet and Octopus, were also tested. Results from the static and dynamic program analysis showed that the three apps did not collect sensitive information such as the IMEI for transaction purposes. The official website of Android Pay and Google Wallet states that the “tokenization” technology is used to create a set of unique identification codes to replace credit cards for transactions, so that the IMEI is not needed for verification. Octopus uses NFC chips on the Octopus cards – a widely-used stored value smart card for making electronic payments in online or offline systems in Hong Kong – for verification.
Alibaba Group replied to enquiries FactWire issued to Taobao, Taobao World and Tmall, stating that they abide by the law in collecting, storing and using information and they value the protection of users’ information. The reply also stated that the collection of IMEI, IMSI, telephone numbers and SIM card information is “an important procedure in carrying out security measures such as users’ identity verification and monetary transactions to combat fraud and ensure security.” For example, it said IMEI could be used to determine whether the account has a risk of being hijacked, and users could be reminded to re-login for security purposes. The reply also stated that the Taobao app does not involve backdoor procedures.
Ant Financial Services Group replied to an enquiry FactWire issued to Alipay, stating that they collect users’ IMEI and IMSI after gaining their consent in order to better safeguard their account security. No replies have been received from WeChat so far.
WeChat’s Privacy Policy states that WeChat would “collect, store and use” users’ personal information, location data as well as log data, including users’ IP addresses, metadata, search terms used, social media profiles visited while using WeChat, people with whom users have communicated with as well as the time, data and duration of their communications, etc. The policy also states that they have gained users’ “consent to the third party use, sharing and transfer” of their Personal Information (both inside and outside of their jurisdiction) and WeChat can “operate and may continue to operate servers in a number of jurisdictions around the world, so the server on which your Personal Information is used and stored may not be in your jurisdiction”.
Cybersecurity and hacking expert Anthony Lai Cheuk-tung said that some governments and law enforcement agencies could deduce one’s behavior by integrating and analyzing one’s information found in the massive database through “Machine Learning”, a technology based on Artificial Intelligence.
“Some dissidents were identified because their IP addresses were collected through WeChat while they were using the app. If the dissidents used Taobao or Alipay, one could identify the transactions they performed,” said Lai.
Lai also stated that a single app may not leak all of one’s information found on the network, such as one’s lifestyle and shopping preferences. From a technical point of view, however, the government could gather all of one’s data from various apps, analyze their behavior, and achieve the goal of surveillance.
The PCPD replied to FactWire’s enquiry, stating that the Personal Data (Privacy) Ordinance (PDO) is of no legal effect outside Hong Kong, and would not comment on the laws and regulations of other countries. The PCPD further stated that if users have agreed to the relevant terms and conditions and privacy policies of the mobile apps which stated that the users’ personal information could be transferred to law enforcement agencies outside of Hong Kong for investigation, it means that users have given consent to the above action.
As to whether the present regulations could prevent or protect users’ personal information from being transferred to servers in the mainland, Wong said that section 33 of the PDO regarding the “Prohibition against transfer of personal data to a place outside Hong Kong” has yet to come into effect. The PCPD encourages data users (app developers and operators) through the “Guidance on Personal Data Protection in Cross-border Data Transfer” to follow the guidelines in safeguarding personal information.
Spokesman of the Progressive Lawyers Group and legal consultant Craig Choy Ki said that Hong Kong has not made laws to ban the transferal of personal information to places outside Hong Kong, and the “Guidance on Personal Data Protection in Cross-border Data Transfer” is of no legal effect. In addition, users have agreed to the terms and conditions of the apps that they downloaded. Therefore, developers and operators “do not have to gain users’ permission before transferring their personal information to the mainland”.
Choy also said that users’ personal information would be regulated by relevant laws in mainland China once the information is stored there, so that information such as user logs could be kept by Chinese law enforcement agencies. Choy added that with the incomprehensive privacy laws in the mainland, some Hong Kong people believe that “information under the protection of the Personal Data (Privacy) Ordinance in Hong Kong is in fact unprotected as they would be under the relevant privacy laws in the mainland”.
Cybersecurity expert Anthony Lai Cheuk-tung stated that users should consider the risk of being put under surveillance when choosing smartphone apps. “Users should not use WeChat if it’s not a must. Try not to use it if you are not doing business in China,” said Lai. He added that users could use two mobile phones and only install such insecure apps as WeChat into their phone for non-daily use, so as to minimize the risk of being put under surveillance. If users are worried that they are being monitored, Lai said that they could use pay-as-you-go SIM cards that do not require real-name registration and refrain from installing Chinese apps if not needed.
China’s State Council issued the “Planning Outline for the Construction of a Social Credit System (2014-2020)” in 2014, which states that every citizen and organization within the Chinese borders would be included in a social credit system by 2020. One’s sincerity in administrative, commercial, social and judicial affairs would be recorded, accessed, scored and filed for the inspection and surveillance of the government or relevant organizations. Based on one’s records, the authorities could make decisions that could impact one’s life, such as whether one could receive tax benefits, choose soft beds in trains, get on a flight, exit the borders, etc.
“Credit construction” is also going to be carried out in the area of Internet applications and services. The Outline stated that one’s behavior on the Internet would be filed as “network credit files” and become information available for “exchange and sharing”. Moreover, an online credit black list system would be established to list enterprises and individuals who committed “grave acts of breaking trust online”. Measures against subjects on the black lists including limitations on their “online conduct and barring sectoral access, and reporting them to corresponding departments for publication and exposure” would be adopted.
More recently, the “Provisions on the Management of Mobile Internet Application Information Services” issued by the Cyberspace Administration of China (CAC) came into effect on August 1 2016. The Provisions stated that mobile Internet app providers have to verify new app users’ mobile phone numbers and other identity information. App providers must record user logs and keep them for at least 60 days. The Provisions also stated that app providers and app store service providers should assist inspection and surveillance by relevant government departments in accordance with the laws.
This story is picked up and reported by the following news media: